Public DNS malware filters to be tested in 2025
How well do the largest public DNS resolvers that protect you against malware domains perform in June 2025? We put them to the test!

As per annual tradition we put a number of public DNS filters to the test. They offer a 'safe' DNS resolver where they block malicious domain names.
New in this test is the recently launched DNS4EU, a DNS resolver created at the initiative of the European Commission.
List of malicious domain names
Once again, we downloaded a list of 76,956 malicious domains from the CERT Poland website. CERT Poland still updates this list daily. We also downloaded a list of malicious domains from URLhaus, good for 3,824 domains. In total, this resulted in a list of 80,762 unique malicious hosts. More than enough to get a good idea of how well or badly the DNS resolvers perform.
Tested DNS resolvers
Our list of DNS resolvers looks like this:
- Cloudflare Public DNS - 1.1.1.1 (for reference, unfiltered)
- ControlD Malware - 76.76.2.1
- Quad9 - 9.9.9.9
- Cloudflare for Families - 1.1.1.2
- UltraDNS Threat Protection - 156.154.70.2
- dns0.eu - 193.110.81.0
- CleanBrowsing Security Filter - 185.228.169.9
- DNS4EU Protective resolution - 86.54.11.1 (new in the test)
Changes compared to our last test of 2024:
- Given the small difference in results with 'dns0.eu', we left 'dns0.eu ZERO' out of the test.
- We removed Norton ConnectSafe from the test since Norton retired this service.
- We also removed Comodo Secure DNS from the test due to disappointing results.
- We added DNS4EU.
How we performed the test
For this test we wrote a simple Bash script. This script did:
- 10 pings to each DNS resolver to obtain an average ping time.
- A test of 5 known websites that are definitely not in the malicious list to confirm the correctness of the DNS resolvers.
- A check of each malicious domain against the unfiltered DNS resolver 1.1.1.1 (Cloudflare) to check whether the domain has at least 1 A-record.
- If at least 1 A-record was found, the domain was tested against all DNS resolvers.
- If the tested DNS resolver returned a valid IP address, this was stored in a CSV.
- If the DNS resolver returned no value or a blackhole IP address, no value was stored in the CSV. In that case, we assumed that the domain is known to the provider as 'malicious'.
Results
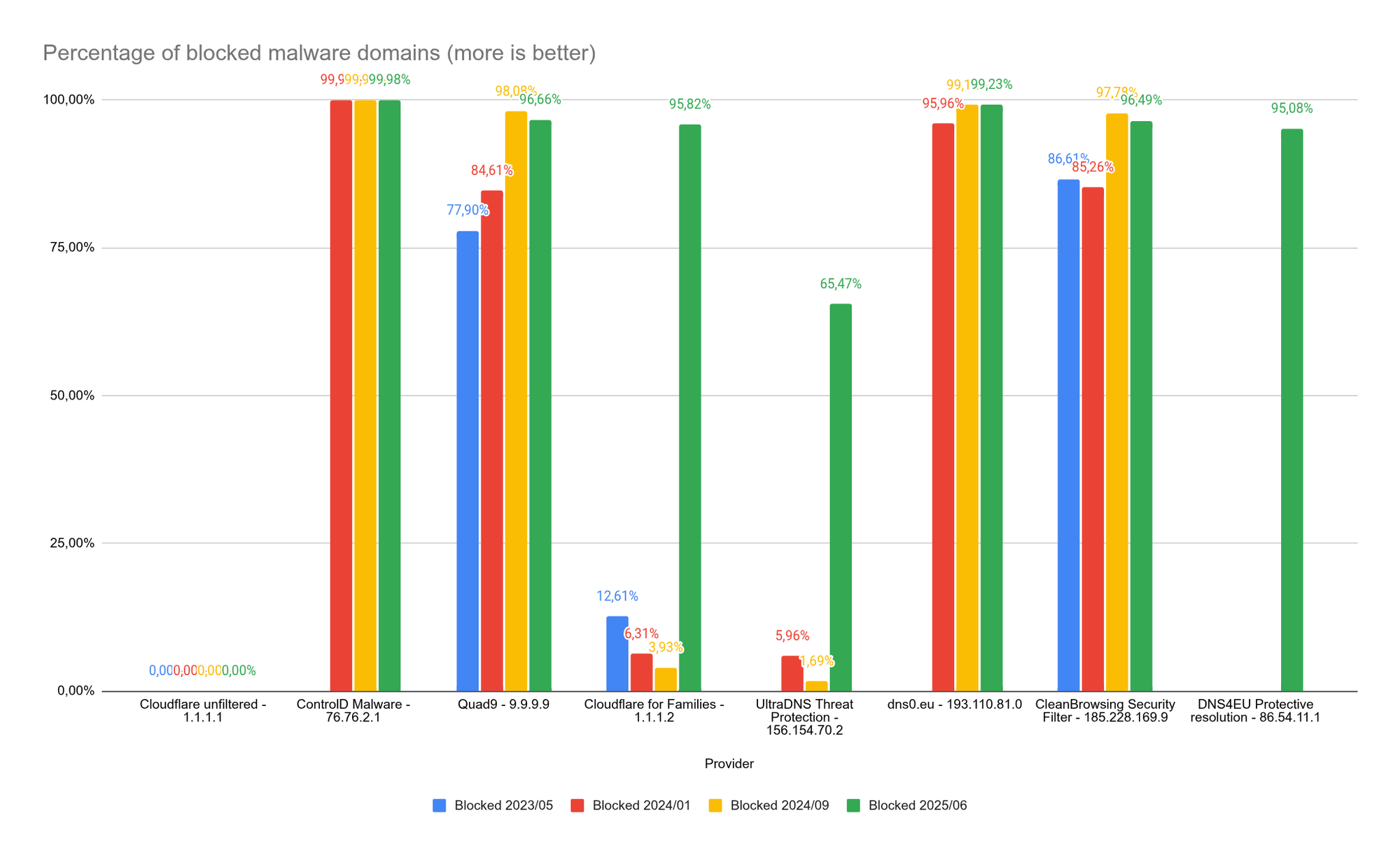
Cloudflare's unfiltered DNS found 39,160 hosts with an A record. These hosts were presented to all DNS resolvers. The table below shows how many hosts with a valid IP address the DNS resolver resolved (not blocked) and did not resolve (blocked).
| Provider | Cloudflare unfiltered | ControlD Malware | Quad9 | Cloudflare for Families | UltraDNS Threat Protection | dns0.eu | CleanBrowsing Security Filter | DNS4EU Protective resolution |
|---|---|---|---|---|---|---|---|---|
| Resolved | 39160 | 7 | 1309 | 1637 | 13520 | 302 | 1373 | 1926 |
| Not resolved | 0 | 39153 | 37851 | 37523 | 25640 | 38858 | 37787 | 37234 |
| Blocked % | 0,00% | 99,98% | 96,66% | 95,82% | 65,47% | 99,23% | 96,49% | 95,08% |
Conclusion
ControlD has scored well in recent years, but this year they have surpassed themselves. Only 7 malicious domains slipped through the cracks of their net.
dns0.eu and CleanBrowsing also achieved excellent results again. We see a small decline for Quad9, but that certainly does not make them less reliable.
Although 'Cloudflare for Families' has been in a downward trend for three times in a row, they have made a phenomenal catch-up. They have clearly tinkered with their filter.
UltraDNS scores the lowest, but has experienced a very strong growth. Not as strong as Cloudflare, but it is a step in the right direction.
DNS4EU, a newcomer, sets a very strong precedent from its first year.
Testing accessibility with RIPE Atlas
RIPE Atlas is a project of RIPE NCC, the organization responsible for the distribution of IP addresses in Europe and the Middle East. They have more than 13,500 so-called 'probes' active worldwide. Probes are single-board computers, comparable to a Raspberry Pi, which are mainly active with consumers. So on private networks behind B2C internet providers. From the RIPE Atlas project, participants can launch 'measurements' on these worldwide probes. Measurements are for example a ping command to get an idea of the accessibility of a service in a certain country, region or continent. More information about this project (and how you can host a probe yourself) can be found at https://atlas.ripe.net.
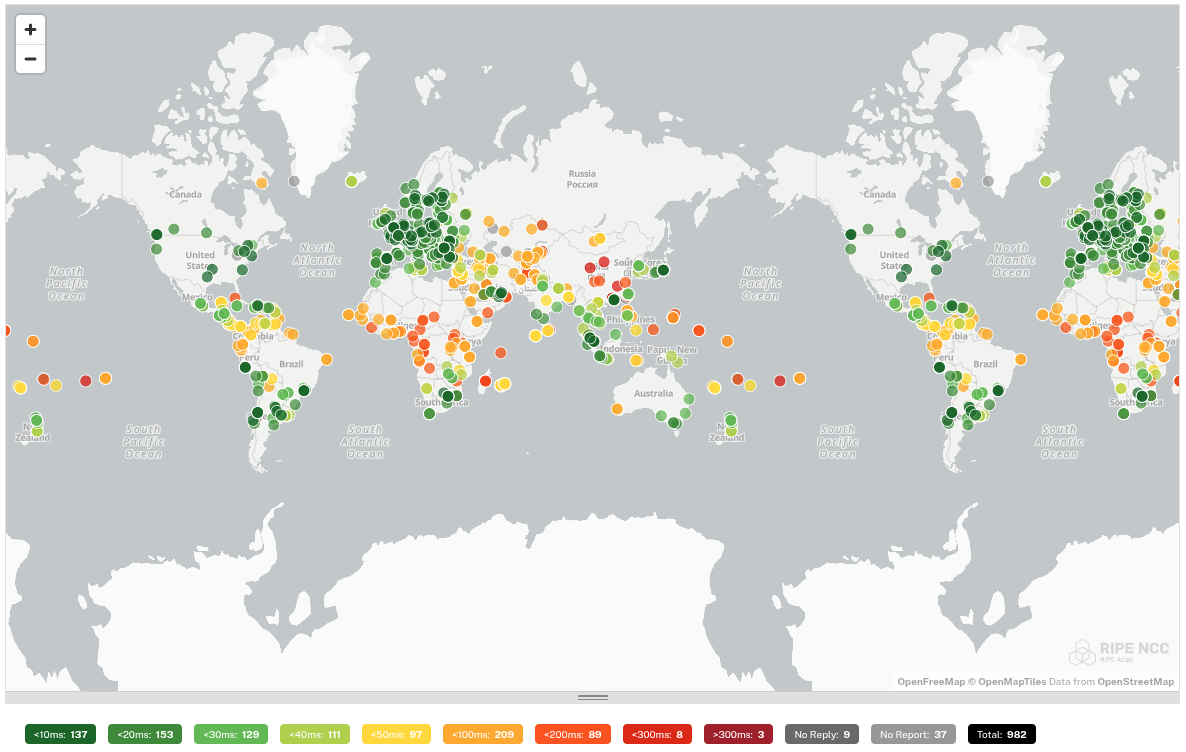
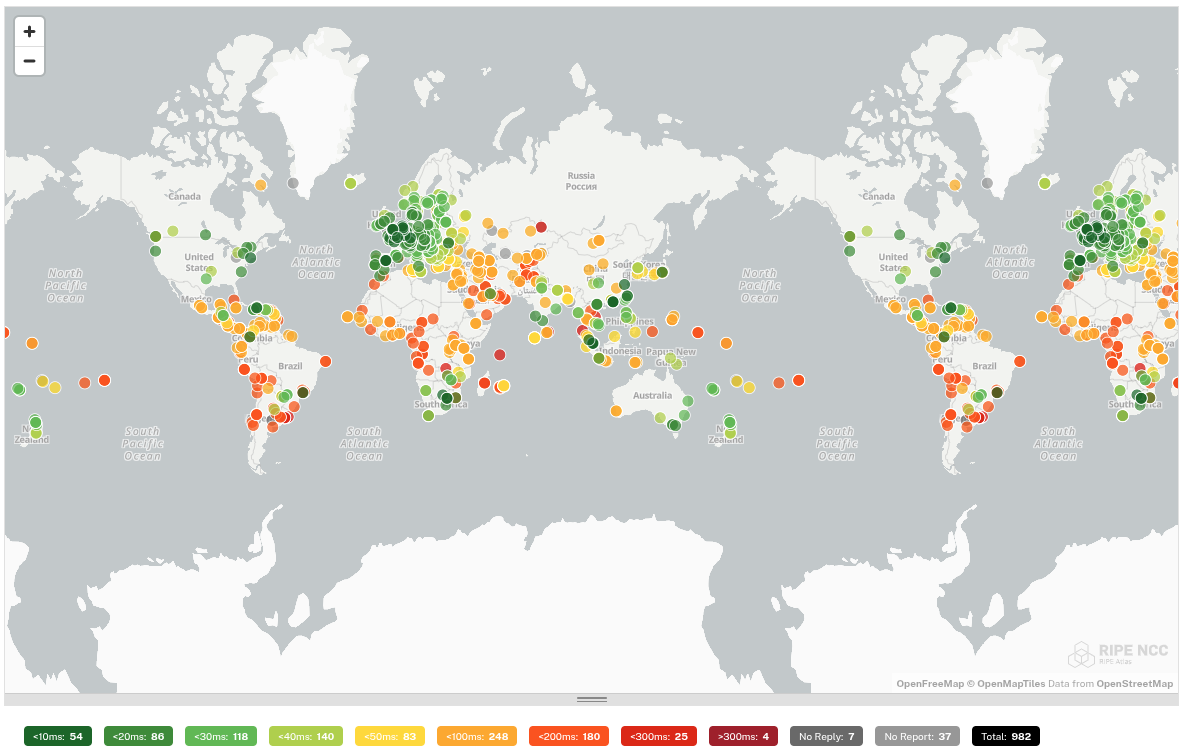
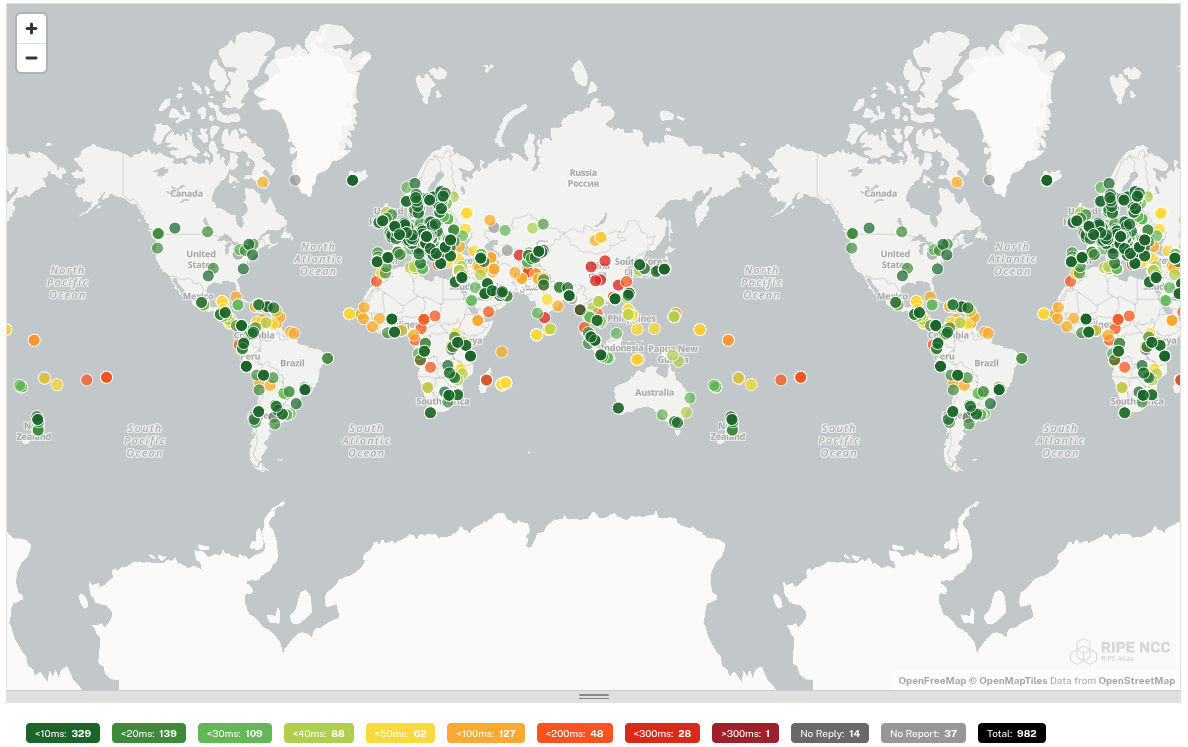
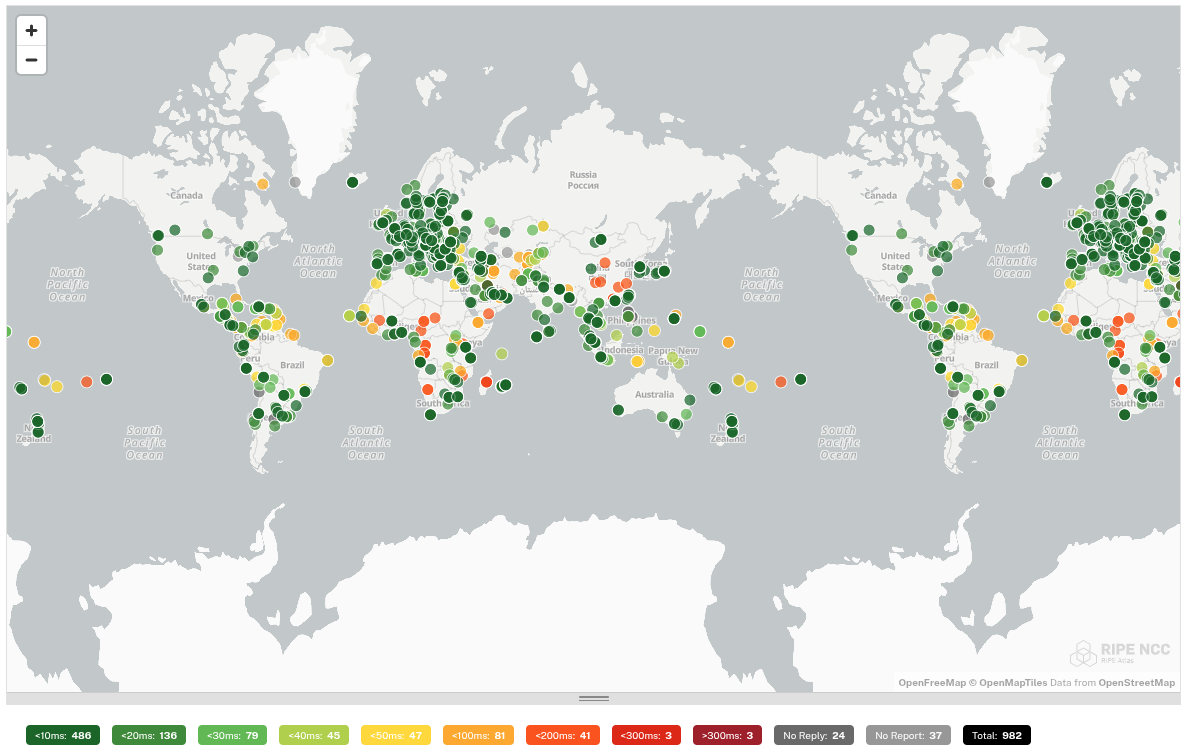
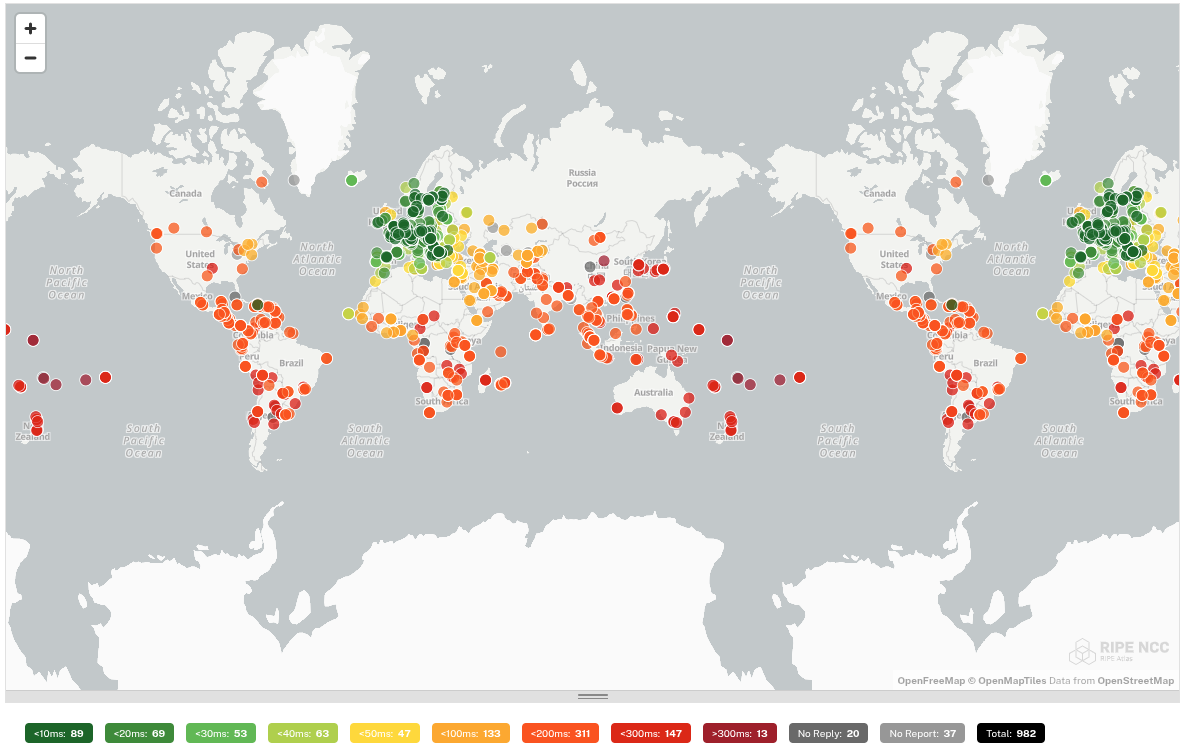
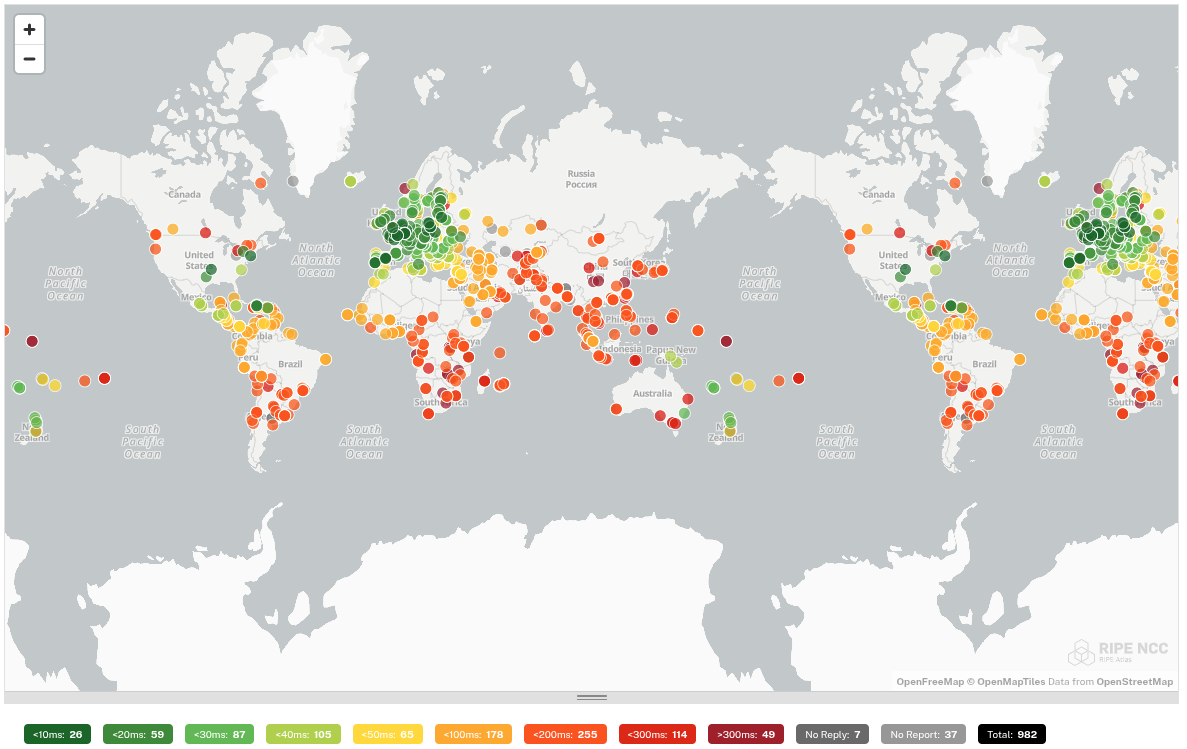
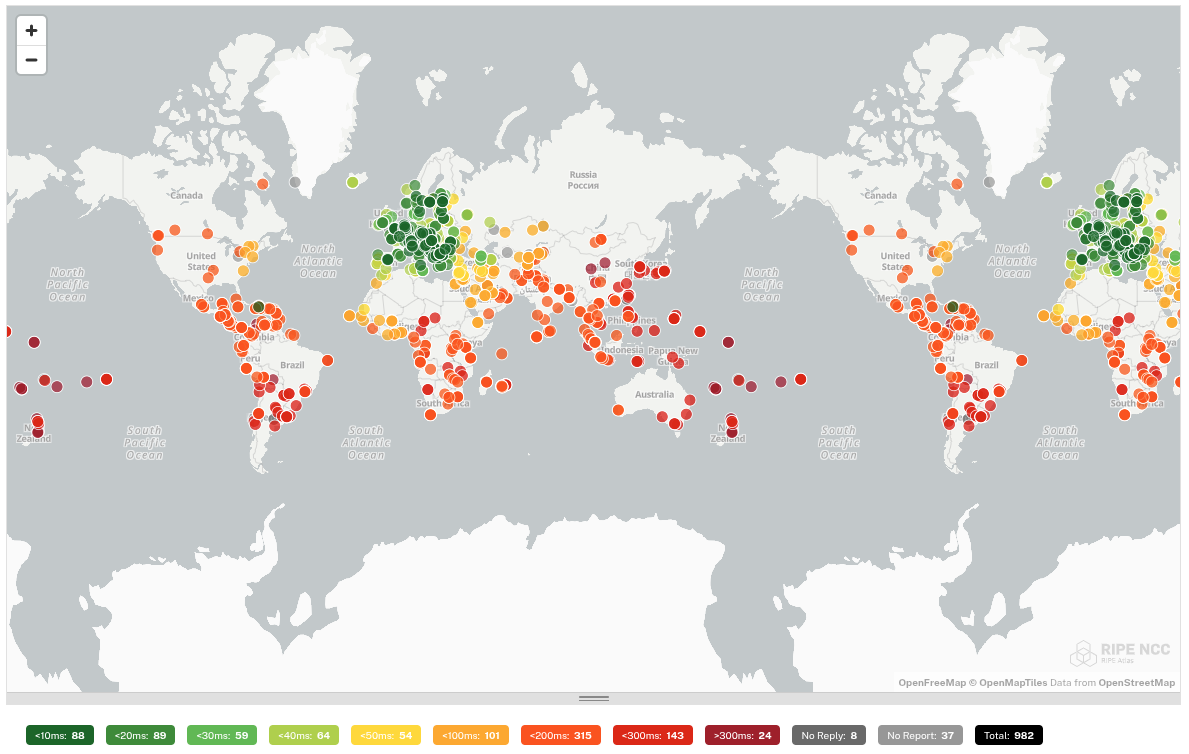
We subjected each tested DNS resolver to a ping command by 1000 probes distributed worldwide. This gives us an idea of how well the DNS resolver is reachable worldwide.
Here is a link to all the results in detail:
In this test, big differences are noticeable. The DNS resolvers of Quad9 and Cloudflare respond worldwide with a low ping. These providers therefore focus on a global audience and not on a specific continent. This is in contrast to e.g. dns0.eu and DNS4EU which are good accessible in Europe, but have a high ping in other continents.
The danger of false positives
Working with third-party malware lists has the disadvantage that domains that are not actually malware may be blocked. This is called 'false positives'.
We downloaded the 'top 1,000' domains from Cloudflare Radar. This is a list of the 1,000 most requested domains worldwide at the Cloudflare unfiltered DNS resolver in the past 7 days. Can we be 100% sure that these domains are not malware domains? No. But since these are the 1,000 largest websites, we can assume this. Therefore, all DNS resolvers should not block these domains.
Of the 1,000 domains, 692 were offered to all DNS resolvers. The result? Only a few were not resolved, which is almost negligible and a fine result.
| Provider | Cloudflare unfiltered | ControlD Malware | Quad9 | Cloudflare for Families | UltraDNS Threat Protection | dns0.eu | CleanBrowsing Security Filter | DNS4EU Protective resolution |
|---|---|---|---|---|---|---|---|---|
| Resolved | 692 | 692 | 692 | 691 | 689 | 692 | 691 | 692 |
| Not resolved | 0 | 0 | 0 | 1 | 3 | 0 | 1 | 0 |
Why couldn't all 1,000 most used domains be tested? Because some domains didn't return an A-record. This is because the domain only uses subdomains as 'CDN' or as 'tracker' for example.
