Public DNS malware filters tested in 2024
How well do the largest public DNS resolvers that protect you against malware domains score in January 2024? We did the test!

Preventing a malware infection within your network is a matter of layered defensive measures. One of those measures is DNS filtering. But since numerous malware domains are added every day, it is impossible to maintain a blacklist yourself. For this you can rely on public DNS resolvers that block malware domains.
In the spring of 2023, we challenged a number of free public DNS resolvers (see this article). What is the situation now in 2024? Are these DNS resolvers performing better or worse than a year ago? We did the test again!
List of malicious domain names
Once again we downloaded a list of 163,196 malicious domains from the CERT Poland website. CERT Poland continues to update this list daily. We have also downloaded a list of malicious domains from URLhaus, representing 8,709 domains. In total, this resulted in a list of 171,905 unique rogue hosts. More than enough to get a good idea of how well or poorly the DNS resolvers are performing.
Tested DNS resolvers
Our list of DNS resolvers looks a little different than last year.
- Google Public DNS - 8.8.8.8 (for reference, unfiltered)
- ControlD Malware - 76.76.2.1 (new in the test)
- Norton ConnectSafe - 199.85.126.10 (new in the test)
- UltraDNS Threat Protection - 156.154.70.2 (new in the test)
- Quad9 - 9.9.9.9
- Cloudflare for Families - 1.1.1.2
- dns0.eu - 193.110.81.0
- dns0.eu ZERO - 193.110.81.9
- CleanBrowsing Security Filter - 185.228.169.9
- Comodo Secure DNS - 8.26.56.26
How we performed the test
We wrote a simple Bash script for this test. This script did:
- 10 pings to each DNS resolver to get an average ping time.
- A test of 5 known websites that are definitely not in the malicious list to confirm the correctness of the DNS resolvers.
- A check of each malicious domain against the unfiltered DNS resolver 1.1.1.1 (Cloudflare) to verify that the domain has at least 1 A-record.
- If at least 1 A-record was found, the domain was tested against all DNS resolvers.
- If the tested DNS resolver returned a valid IP address, it was stored in a CSV. If the DNS resolver returned no value or the IP address 0.0.0.0 or 127.0.0.1, then no value was stored in the CSV.
If the DNS resolver returned no value or the value 0.0.0.0 or 127.0.0.1, that was a sign that it was not resolving the domain. In that case, we assume that the domain is known to the provider as 'malicious'.
Results
Cloudflare found an A-record among 51,507 hosts. These hosts were offered to all DNS resolvers. The table below shows how many hosts with a valid IP address have been resolved (not blocked) and not resolved (blocked) by the DNS resolver.
| Provider | Google Public DNS | ControlD Malware | Norton ConnectSafe | UltraDNS Threat Protection | Quad9 | Cloudflare for Families | dns0.eu | dns0.eu ZERO | CleanBrowsing Security Filter | Comodo Secure DNS |
|---|---|---|---|---|---|---|---|---|---|---|
| Resolved | 51389 | 32 | 51369 | 51397 | 7925 | 48259 | 2082 | 2015 | 7593 | 51399 |
| Not resolved | 118 | 51475 | 138 | 110 | 43582 | 3248 | 49425 | 49492 | 43914 | 108 |
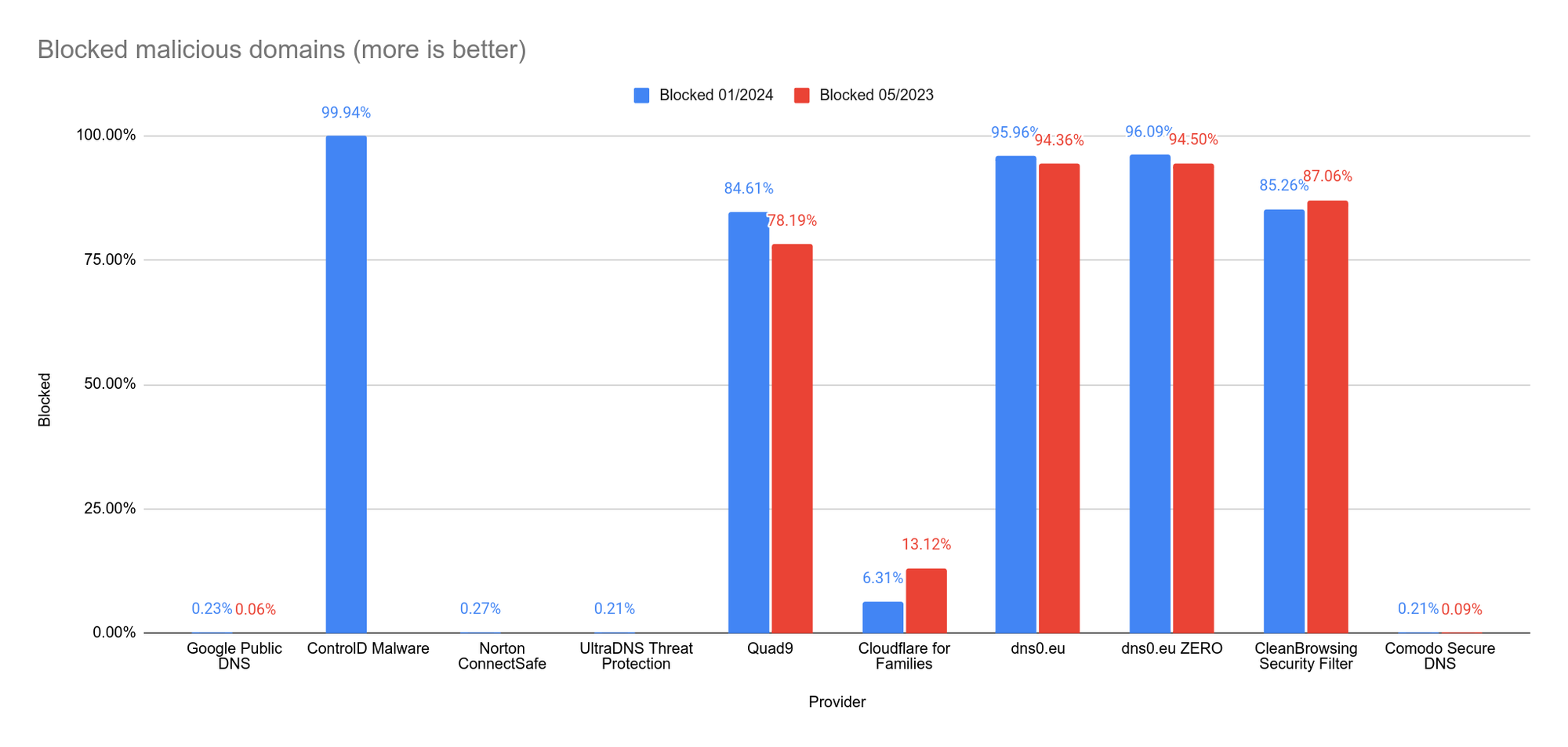
| Blocked | 0.23% | 99.94% | 0.27% | 0.21% | 84.61% | 6.31% | 95.96% | 96.09% | 85.26% | 0.21% |
In the graph below we have added the 2023 results for comparison (in red).
Conclusion
Newcomer in this list 'ControlD Malware' scores surprisingly well. With the exception of only 32 domains, ControlD blocks all domains. DNS0 scores better than last year and Quad9 is also making a big leap forward. Unfortunately, 'Cloudflare for Families' is in sharp decline.
Newcomers 'Norton ConnectSafe' and 'UltraDNS Threat Protection' may need to thoroughly check their malware filter. 'Comodo Secure DNS' is also still doing just as poorly as last year.
The danger of false positives
Working with third-party malware lists has the disadvantage that domains may also be blocked that are not actually malware. This is called 'false positives'.
We downloaded the 'top 1,000' domains from Cloudflare Radar. This is a list of the top 1,000 globally requested domains on the Cloudflare unfiltered DNS resolver over the past 7 days. Can we be 100% sure that these domains are not malware domains? No. But since these are the 1,000 largest websites, we can assume this. Therefore, all DNS resolvers should not block these domains.
Of the 1,000 domains, 706 were offered to all DNS resolvers. The result? Only a few were not resolved, which is almost negligible and an excellent result.
| Provider | Google Public DNS | ControlD Malware | Norton ConnectSafe | UltraDNS Threat Protection | Quad9 | Cloudflare for Families | dns0.eu | dns0.eu ZERO | CleanBrowsing Security Filter | Comodo Secure DNS |
|---|---|---|---|---|---|---|---|---|---|---|
| Resolved | 706 | 705 | 706 | 706 | 706 | 706 | 706 | 705 | 704 | 703 |
| Not resolved | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 1 | 2 | 3 |
Why couldn't all 1,000 domains be tested? Because some domains did not return an A-record. This is because the domain, for example, only uses subdomains such as 'CDN' or 'tracker'.
