Public DNS malware filters tested
How well do public DNS resolvers that claim to block malware domains really score? Which provider is the safest? We did the test!

We have tested a large number of free public DNS resolvers. To use these DNS resolvers, no account needs to be created. We tested both unfiltered and filtered DNS resolvers.
List of malicious domain names
We downloaded a list of 118.623 malicious domains from the CERT Poland website. CERT Poland updates this list daily and makes it available free of charge with the aim that ISPs and system administrators can use this list to protect their network.
We downloaded the URLhaus list of 11.902 malicious domains from abuse.ch. The purpose of the abuse.ch project is to collect, track and share malware URLs to help network administrators and security analysts protect their network and customers from cyber threats.
These two lists were merged into a list of 130.525 malicious hosts (a combination of both root domains and subdomains).
Tested DNS resolvers
The DNS resolvers we subjected to this test are:
- Google Public DNS - 8.8.8.8 (unfiltered)
- Telenet - 195.130.130.139 (unfiltered, a local Belgian ISP)
- Proximus - 91.183.123.173 (unfiltered, a local Belgian ISP)
- OpenDNS - 208.67.222.222 (unfiltered)
- Quad9 - 9.9.9.9 (malicious domain filter)
- Cloudflare for Families - 1.1.1.2 (malware filter)
- dns0.eu - 193.110.81.0 (malicious domain filter)
- dns0.eu ZERO - 193.110.81.9 (extra malicious domain filter)
- CleanBrowsing Security Filter - 185.228.168.9 (malicious domain filter)
- Comodo Secure DNS - 8.26.56.26 (malicious domain filter)
In principle, the unfiltered DNS resolvers should resolve all domains and return the corresponding IP address. The DNS resolvers that filter the requests should return an empty or a 0.0.0.0 IP address, making the domain unreachable.
On which we do not judge the DNS resolvers
When you choose a DNS resolver, it is important not only to consider the number of blocked domain names from this test. Also keep in mind:
- Speed. Your network uses DNS all the time, so the faster the DNS resolver is, the better.
- Privacy. Are logs kept of your DNS requests that can be linked to you? What legislation do they fall under? How do they deal with requests from governments (do they have a transparency report?)?
- Reliability. Do they have DNS servers in your area? How robust is their infrastructure? What is their uptime history? Do they keep their blocklists up to date?
- Self control. The tested DNS resolvers are all public DNS resolvers that do not require an account. You therefore have no option for whitelisting or blacklisting domains. If this is a requirement, you should look out for paid DNS resolvers.
How we performed the test
We wrote a simple Bash script for this test. This script did:
- 10 pings to each DNS resolver to get an average ping time.
- A test of 5 known websites that are definitely not in the malicious list to confirm the correctness of the DNS resolvers.
- A check of each malicious domain against the unfiltered DNS resolver 1.1.1.1 to verify that the domain has at least 1 A record.
- If at least 1 A record was found, the domain was tested against all DNS resolvers.
- If the tested DNS resolver returned a valid IP address, it was stored in a CSV. If the DNS resolver returned no value or the IP address 0.0.0.0 or 127.0.0.1, then no value was stored in the CSV.
If the DNS resolver returned no value or the value 0.0.0.0 or 127.0.0.1, that was a sign that it was not resolving the domain. In that case, we assume that the domain is known to the provider as 'malicious'.
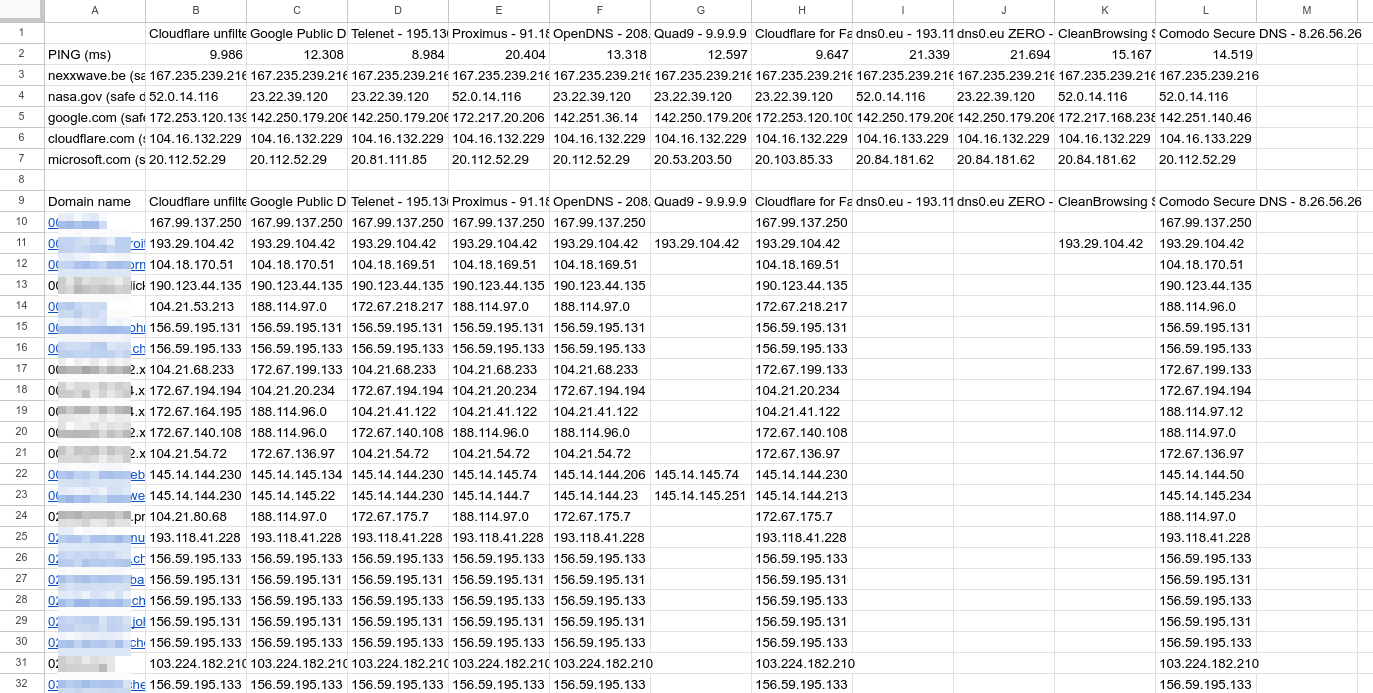
Test results
Cloudflare found an A record at 44.542 hosts. These hosts were then tested against the public DNS resolvers. The table below shows in numbers how many hosts with a valid IP address the DNS resolver returned and what percentage was therefore blocked. So the less valid hosts are routed, the better.
| Provider | Cloudflare unfiltered | Google Public DNS | Telenet | Proximus | OpenDNS | Quad9 | Cloudflare for Families | dns0.eu | dns0.eu ZERO | CleanBrowsing Security Filter | Comodo Secure DNS |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Resolved hosts | 44542 | 44516 | 44387 | 44458 | 44493 | 9713 | 38699 | 2510 | 2452 | 5762 | 44502 |
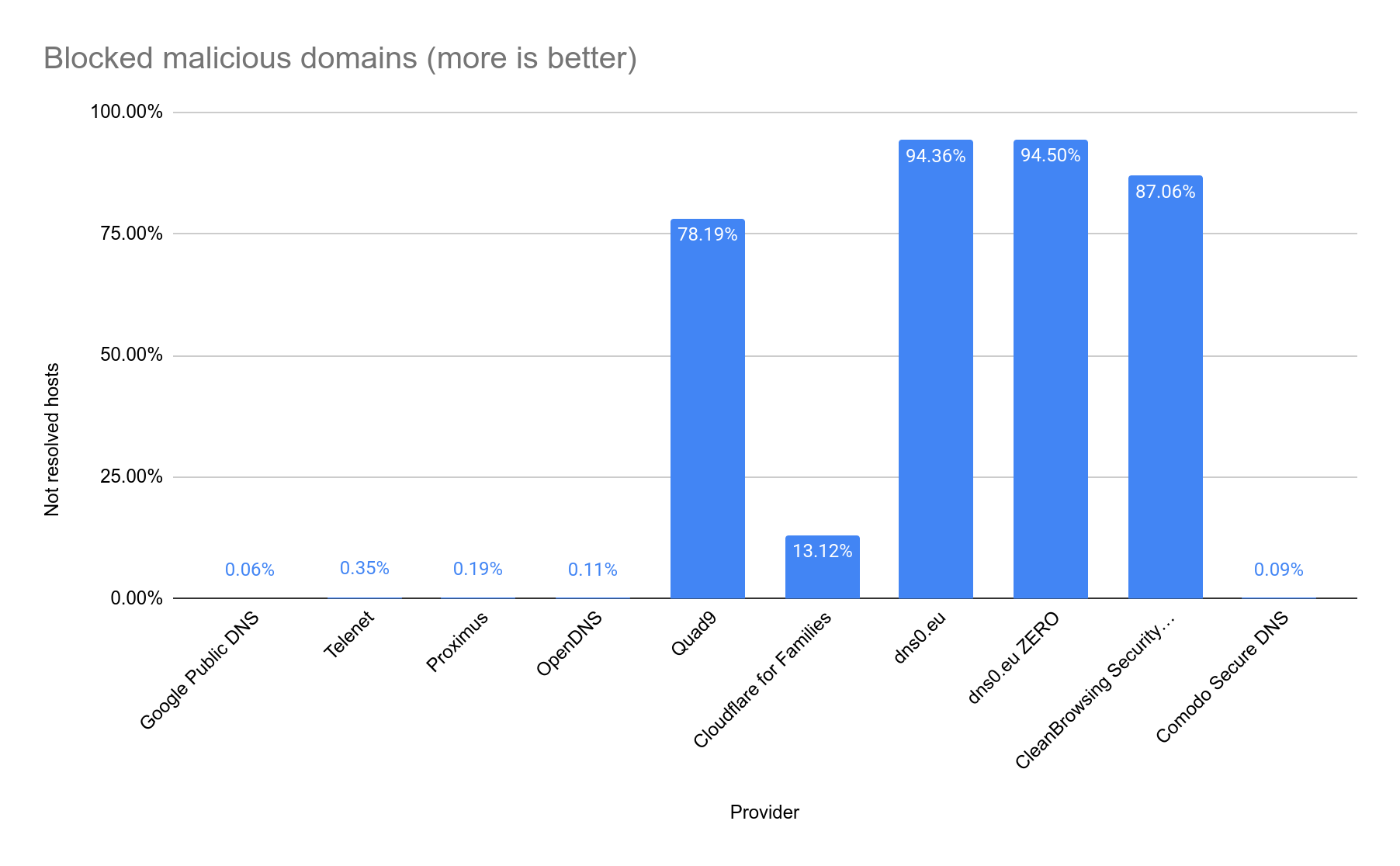
| Not resolved hosts | 0.00% | 0.06% | 0.35% | 0.19% | 0.11% | 78.19% | 13.12% | 94.36% | 94.50% | 87.06% | 0.09% |
Both dns0.eu filters and CleanBrowsing Security Filter score best with the most blocked records. Quad9 rounds out the top four. But then a big leap follows.
It is normal that the unfiltered DNS resolvers score poorly.
Surprisingly, Cloudflare for Families only manages to block 13.12% of domains. Comodo Secure DNS turns out to be not that secure at all with its 0.09% of domains it recognizes as a malicious host.
Background information on the tested public DNS resolvers
Quad9
Quad9 is originally an American (California) DNS provider, but moved its headquarters to Zurich, Switzerland in 2021 so that they would fall under the strictly regulated Swiss privacy law and no longer under the American law (if you want to know more about that, read this article).
Quad9 was founded in 2016 and is a not-for-profit foundation. Their goal is to be a secure, fast and private DNS resolver that blocks malware, spyware, botnets and phishing domains.
Quad9 works with 'Threat Intelligence' partners to maintain an up-to-date list of malicious domains. Partners in this include DomainTools, ECHAP, Netlab360, AbuseCH, IBM X-Force, SwitchCH, H-ISAC and F-Secure. They have a PoP at more than 150 locations in 90 countries, mainly at Internet Exchange points such as the AMS-IX.
Website: www.quad9.net
Cloudflare for Families
The well-known Cloudflare DNS resolver 1.1.1.1 does not use a filter. Since the introduction of '1.1.1.1 for Families' in 2020, they do provide IP address 1.1.1.2 with a 'malware protection' filter.
In addition to this free DNS resolver, they also offer Cloudflare One for companies, where you can manage the DNS filter.
Website: 1.1.1.1/family
DNS0.eu
dns0.eu is a French non-profit organization founded in 2022 by co-founders of NextDNS. They focus entirely on European users and therefore only have DNS servers in European countries. They currently have servers in 55 data centers spread across 27 European cities.
dns0.eu filters for malicious domains ranging from phishing websites to Command & Control (C&C) servers. In addition, with their 'ZERO' filter they filter even harder on typosquatting, DNS rebinding, crypto jacking, parked domains, new active domains, etc.
They obtain their information from malicious domains from their 'Thread Intelligence' partners. These include NetxtDNS, AbuseCH, Shreshta, Lionic, gandi.net, Red Flag Domains, Certgo, Anexia, and GCore.
Website: www.dns0.eu
CleanBrowsing
CleanBrowsing is based in Texas (United States). They offer subscriptions for both families and businesses to provide their filtered DNS service. In addition to paying subscriptions, they also have a free DNS resolver that filters for phishing, spam and malware domain names.
Unfortunately, we couldn't find out on what information they block domains.
Website: www.cleanbrowsing.org
Comodo Secure DNS
Comodo, best known for SSL/TLS certificates, also offers a free filtered DNS resolver since the early 2000s. They have their DNS infrastructure in over 25 countries (which they do not list). To find malicious domains, they rely on their own Thread Intelligence Research Lab that analyzes more than 190 drawers worldwide.
Website: www.comodo.com/secure-dns
